A known security hole in the networking protocol used by cellphone providers around the world played a key role in a recent string of attacks that drained bank customer accounts.
The unidentified attackers exploited weaknesses in Signalling System No. 7(SSN7), a telephony signaling language that more than 800 telecommunications companies around the world use to ensure their networks interoperate. SS7, as the protocol is known, makes it possible for a person in one country to send text messages to someone in another country. It also allows phone calls to go uninterrupted when the caller is traveling on a train.
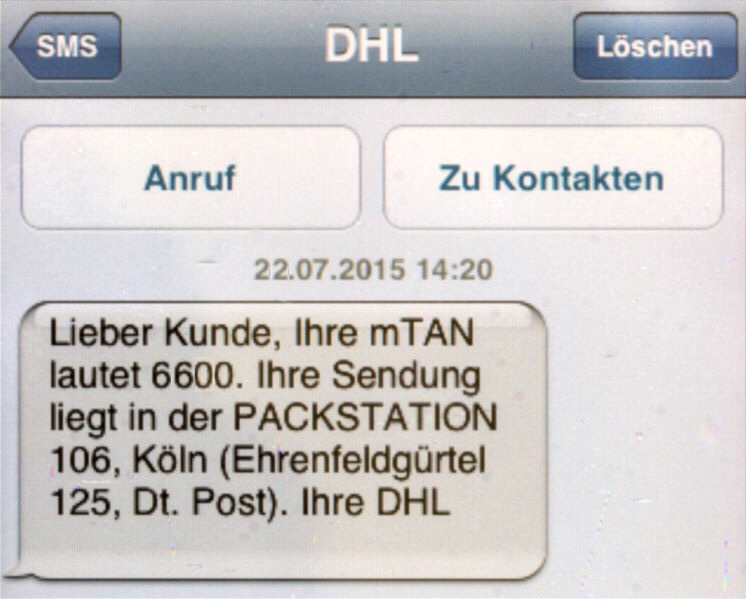
Thieves exploited SS7 weaknesses to bypass two-factor authentication banks used to prevent unauthorized withdrawals from online accounts, the German-based newspaper Süddeutsche Zeitung reported. Specifically, the attackers used SS7 to redirect the text messages the banks used to send one-time passwords. Instead of being delivered to the phones of designated account holders, the text messages were diverted to numbers controlled by the attackers. The attackers then used the mTANs—short for “mobile transaction authentication numbers”—to transfer money out of the accounts.
The interception of the mTANs came only after attackers had compromised bank accounts using traditional bank-fraud trojans. These trojans infect account holders’ computers and steal the passwords used to log in to bank accounts. From there, attackers could view available balances, but they were prevented from making transfers without the one-time password the bank sent as a text message. In the past, attackers have obtained mTANs by obtaining a duplicate SIM card that allows them to take control of the bank customer’s phone number. SS7-facilitated compromises, by contrast, can be done remotely on a much larger quantity of phone numbers.
Read More
Source : Arstechnica