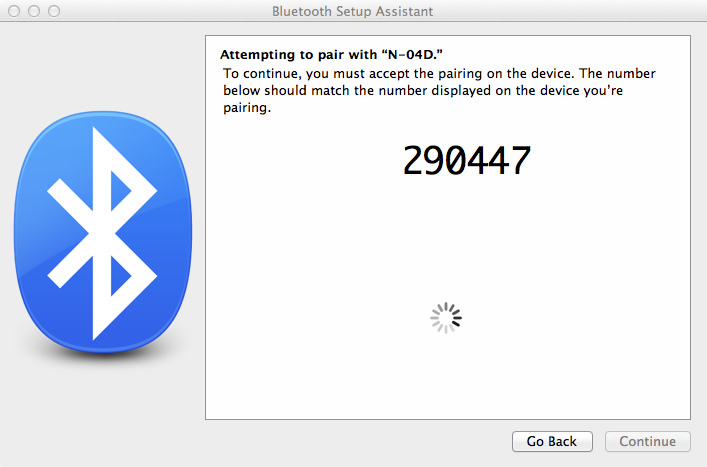
Bluetooth combines Simple Secure Pairing or LE Secure Connections with principles of elliptic curve mathematics to allow devices that have never connected before to securely securely establish a secret key needed for encrypted communications.
The attack uses a newly developed variant of what cryptographers call an invalid curve attack to exploit a major shortcoming in the Bluetooth protocol that remained unknown for more than a decade
Source: arstechnica.com